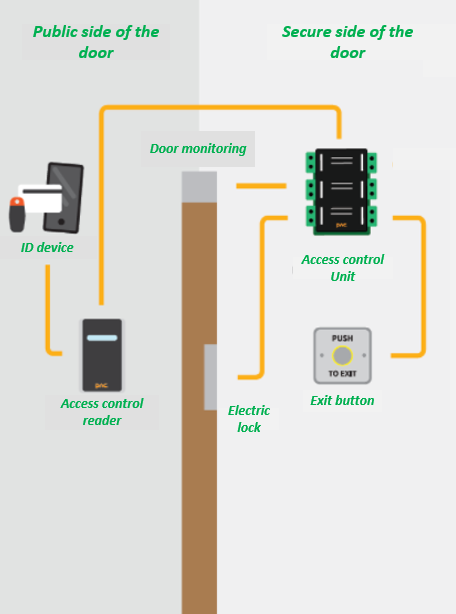
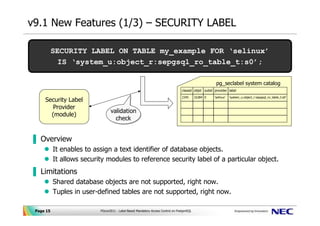
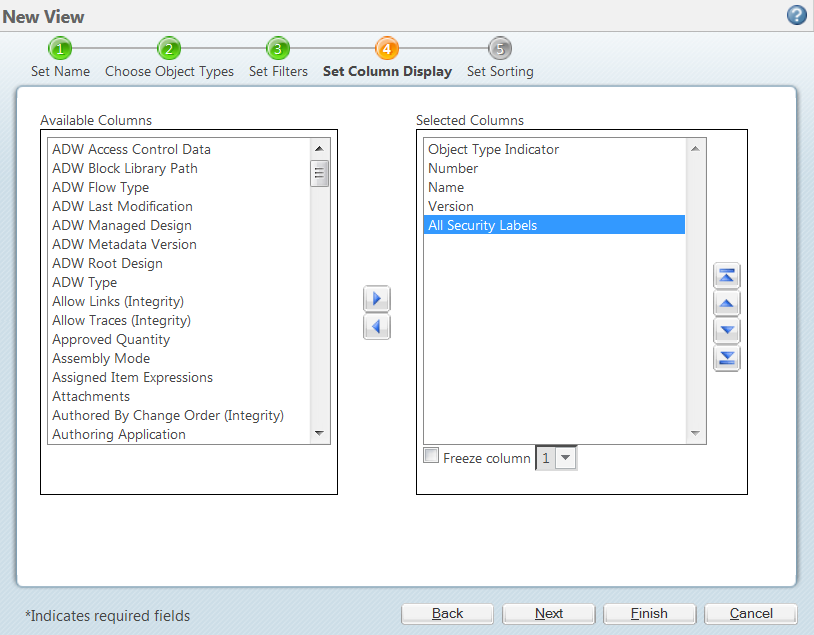
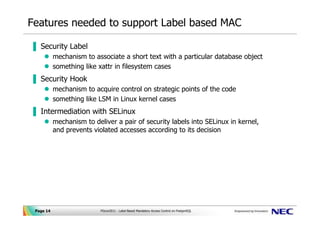
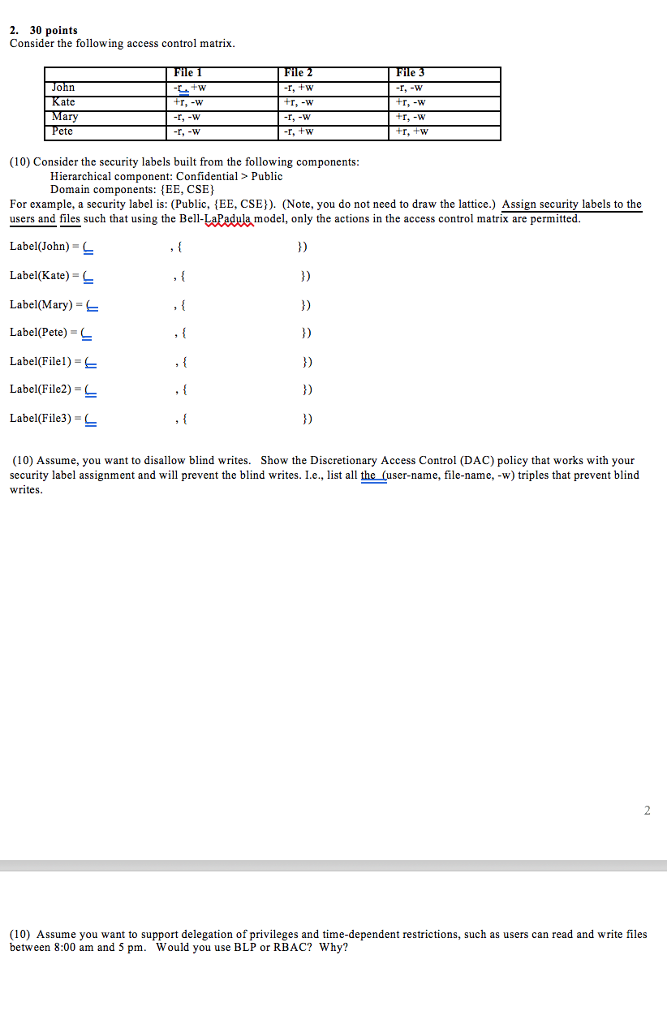
42 security labels access control
Search Results - CDW Specifications are provided by the manufacturer. Refer to the manufacturer for an explanation of print speed and other ratings. Forms in HTML documents - W3 17.1 Introduction to forms. An HTML form is a section of a document containing normal content, markup, special elements called controls (checkboxes, radio buttons, menus, etc.), and labels on those controls.
Create and manage access control lists (ACLs) - Google Cloud Nov 08, 2022 · Refer to Access Control Scopes for a list of supported values for Entity. Enter a value in Name. Name identifies a specific user, group, or other entity type. Refer to Access Control Scopes for a list of supported values for Name. Together, Entity and Name define who the permission applies to. Choose a value in Access.
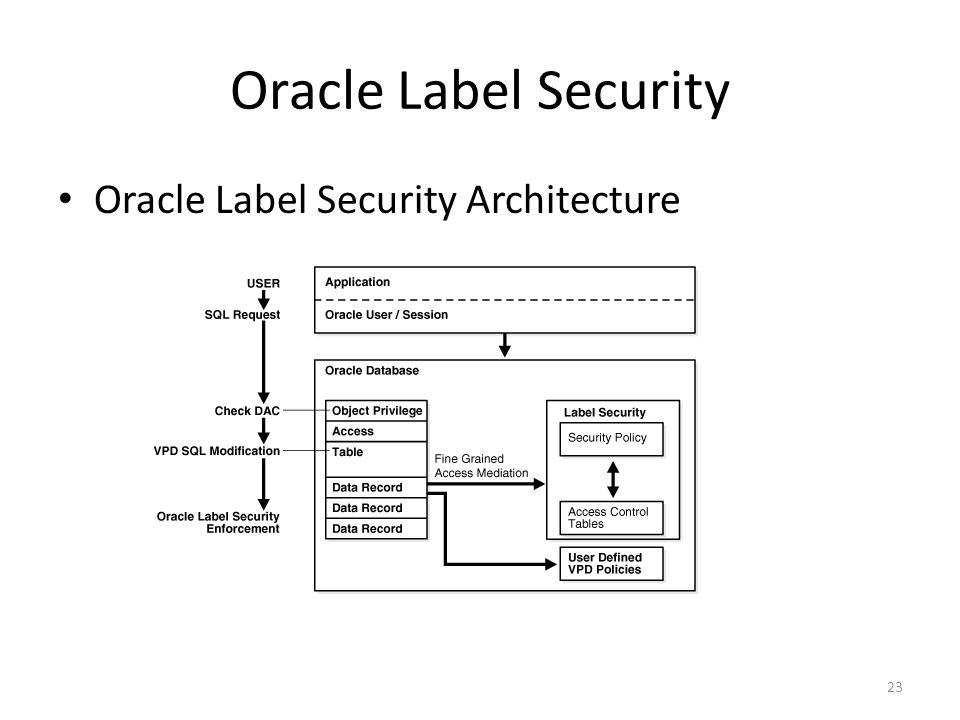
Security labels access control
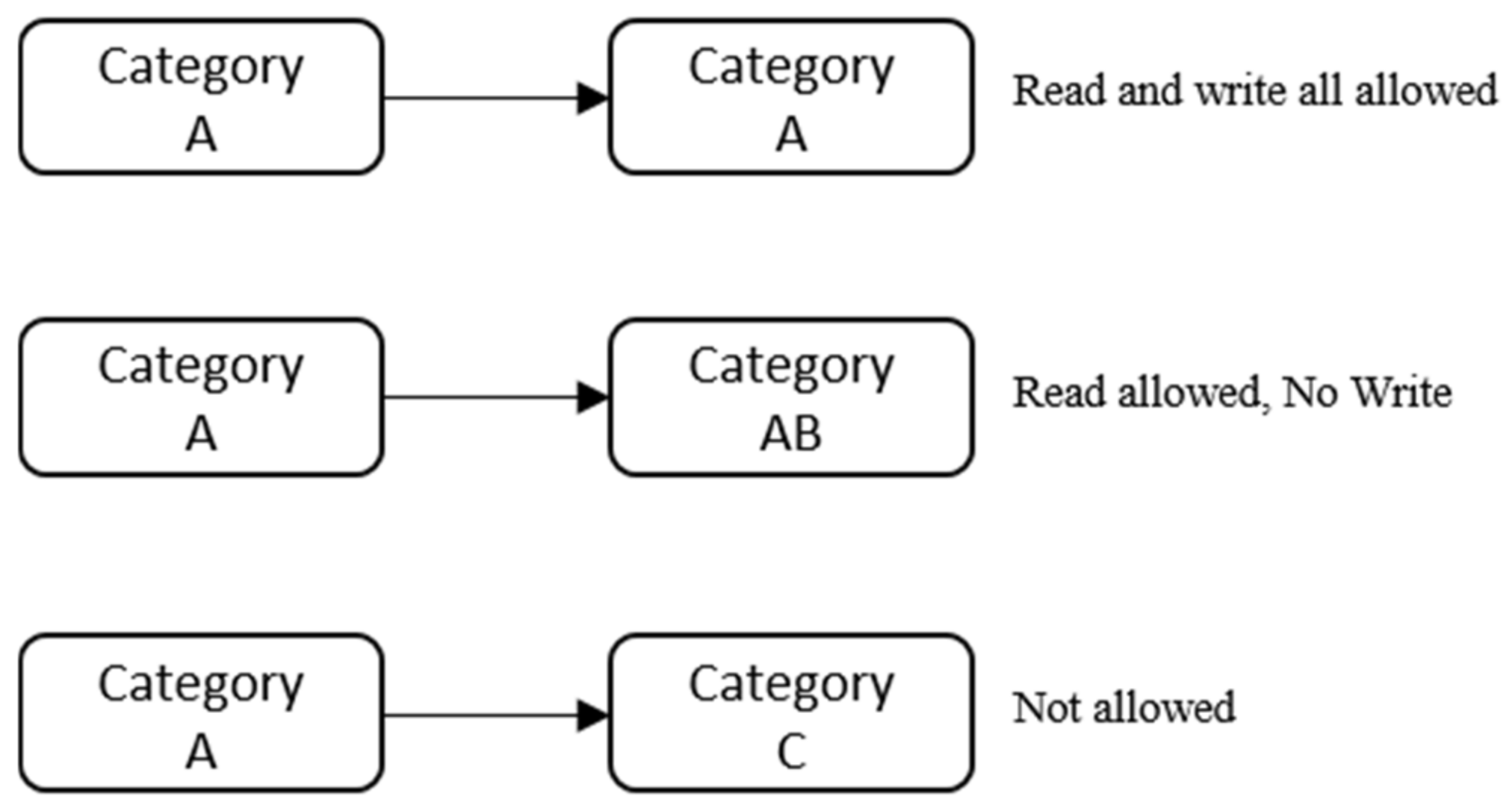
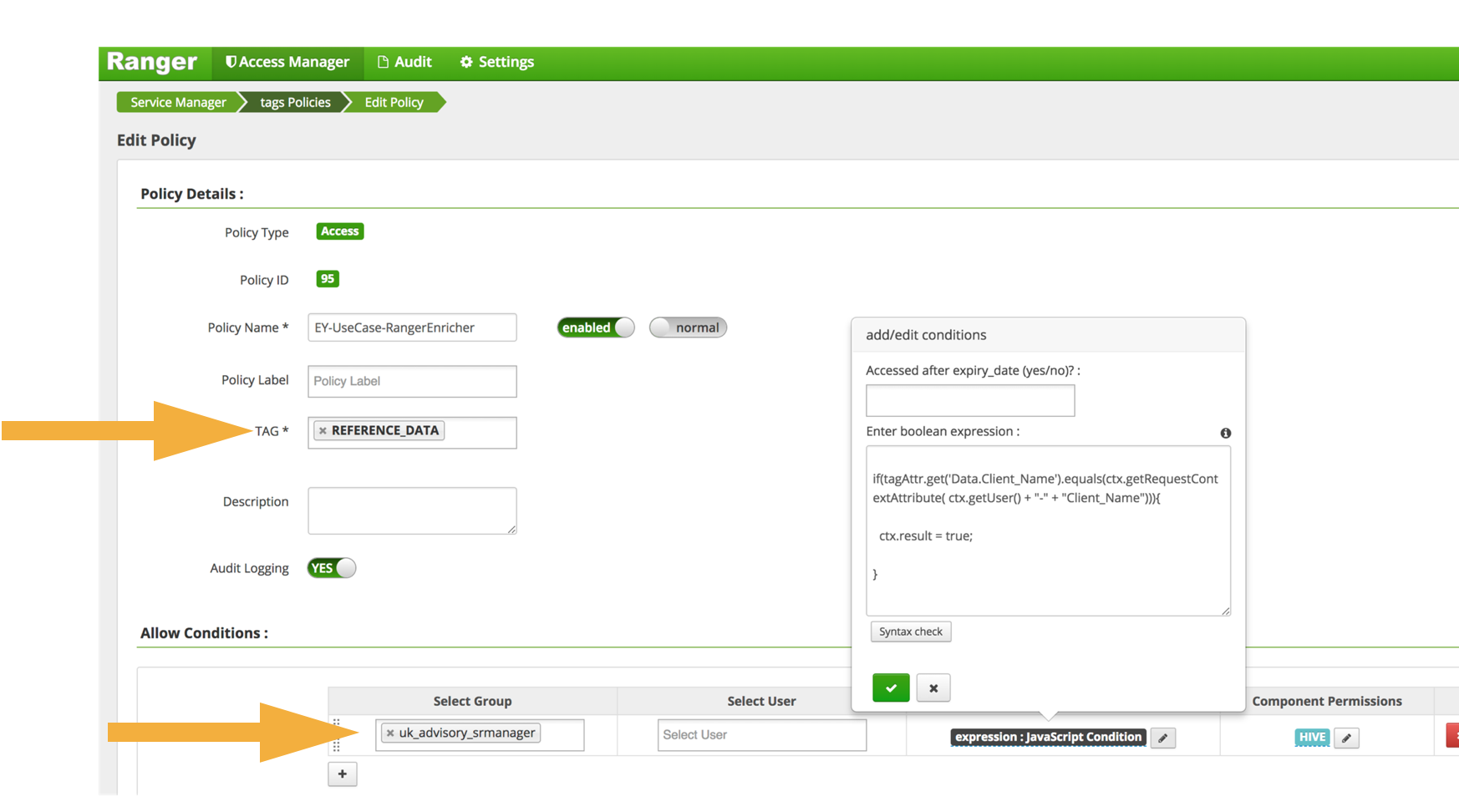
Overview of access control | Cloud Storage | Google Cloud Nov 04, 2022 · ACLs control permissioning only for Cloud Storage resources and have limited permission options, but allow you to grant permissions per individual objects. You most likely want to use ACLs for the following use cases: Customize access to individual objects within a bucket. Migrate data from Amazon S3. Additional access control options Mandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] . Access Control Models: MAC, DAC, RBAC, & PAM Explained Jul 29, 2021 · Management burden — A dedicated organizational structure must manage the creation and maintenance of security labels. What is discretionary access control (DAC)? Discretionary access control decentralizes security decisions to resource owners. The owner could be a document’s creator or a department’s system administrator.
Security labels access control. Roles and role groups in the Microsoft 365 Defender and ... Nov 03, 2022 · These people can perform only the tasks that you explicitly grant them access to. To access these portals, users need to be a global admin or a member of one or more security or compliance role groups. Permissions in these portals are based on the role-based access control (RBAC) permissions model. Access Control Models: MAC, DAC, RBAC, & PAM Explained Jul 29, 2021 · Management burden — A dedicated organizational structure must manage the creation and maintenance of security labels. What is discretionary access control (DAC)? Discretionary access control decentralizes security decisions to resource owners. The owner could be a document’s creator or a department’s system administrator. Mandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] . Overview of access control | Cloud Storage | Google Cloud Nov 04, 2022 · ACLs control permissioning only for Cloud Storage resources and have limited permission options, but allow you to grant permissions per individual objects. You most likely want to use ACLs for the following use cases: Customize access to individual objects within a bucket. Migrate data from Amazon S3. Additional access control options

retail security anti-theft 58khz eas soft tag strips sticker am dr label for security door eas am anti theft system(1000 pieces)


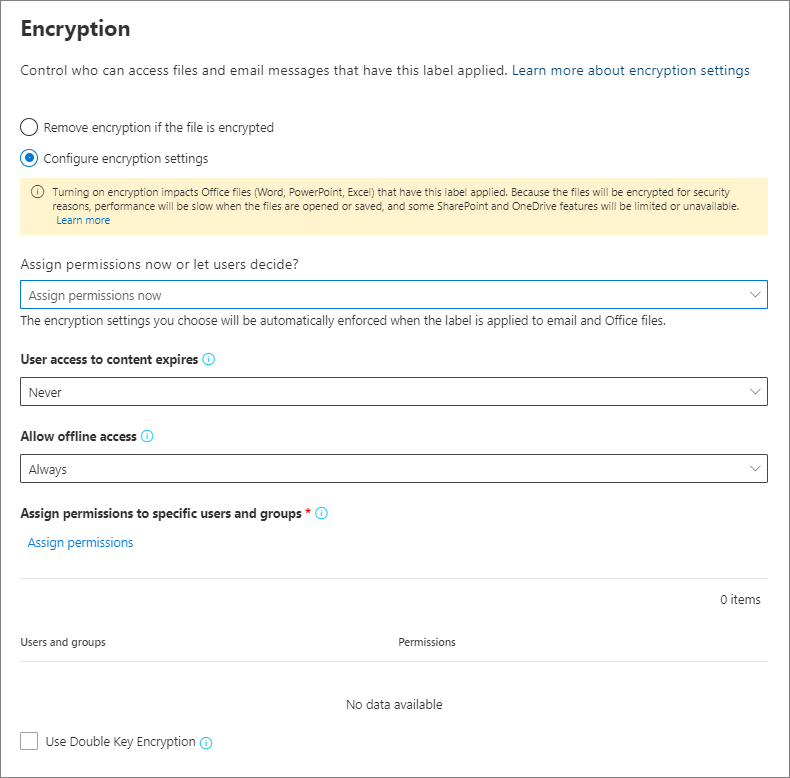
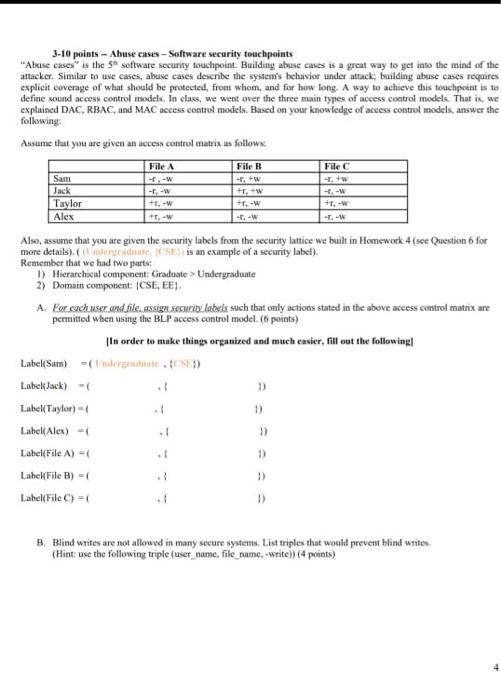



















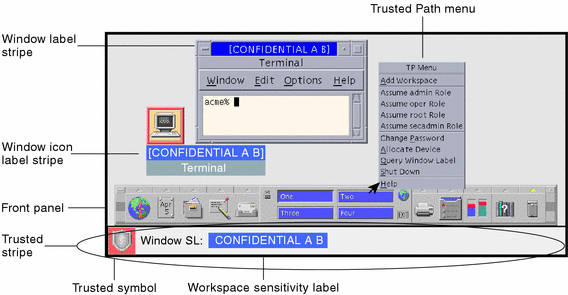

Post a Comment for "42 security labels access control"